1 Introduction
Location information about wireless devices is valuable due to its crucial role in data collection, reliable communications, resource management, emergency services/maintenance, and other important functions of wireless systems[1]. At the same time, security issues in location based systems have received increasing attention[2]. Thus, the method of utilizing the location of a device to achieve security management in location based systems is becoming a focus nowadays.
It is well known that in classic cryptography a party holds some credentials so that its identity, access authority, etc. can be determined. Usually, the credentials consist of the following parts: a registered identity (e. g. , an email address), secret knowledge (e. g. , a pre-shared key or a password), authenticated information (e. g. , a certification issued by CA), a trusted computing base (e. g. , a TPM[3]), biometric data (e. g. , a fingerprint) and so on. However, the location of a device or a user, which is an important piece of information, cannot be used as a credential and applied to realize cryptographic tasks in classic cryptography.
At CRYPTO 2009, Chandran, et al. [4]first introduced the notion of position based cryptography, in which the credential of a party comes from its geographic location. At the same time, the design of secure cryptographic protocols using location as a credential such as secure positioning and position based key exchange, was also investigated. Unfortunately, as a vital primitive in position based cryptography, secure positioning has been proven to have no secure position protocol under collusion attacks without set-up assumptions. As a result, none of the position based cryptographic tasks, including position based key exchange, can be carried out without setup assumptions. In the BRM (Bounded Retrieval Model), Chandran et al. propose secure positioning protocols resistant to collusion attacks. They also propose a secure position based key exchange protocol in the BRM[4]. Subsequently, some position based cryptographic protocols have been proposed in the quantum model[5,6,7]. Recently, the composition security of position based cryptography has also been investigated in universally composable security models[8,9].
PbKE (Position based Key Exchange), which can establish a secret key between a prover located at a valid position and one verifier (or all of the verifiers), is one of the fundamental tasks in position based cryptography. The position based key exchange protocol proposed by Chandran[4]can only realize key establishment between prover and verifier, which is called the p2v (Prover-to-Verifier) mode.
Besides the p2v mode, position based key exchange between two provers, called p2p (Prover-to Prover) mode, should also be considered one of the most important tasks in position based cryptography [10].
This paper investigates the security definitions and the implementations of position based key exchange in two modes. Our contributions are shown below. In particular.
1) To begin with, we distinguish between the two modes of position based key exchange in position based cryptography: the p2v mode and the p2p mode.
2) Then we present the security definitions of position based key exchange. The p2v mode guarantees that one prover (located at one valid position) can share a secret key with the verifiers against the colluding adversaries. In contrast, the p2p mode guarantees that one prover (located at one valid position) can share a secret key with another prover (located at another valid position), while colluding adversaries cannot access any information about the shared key.
3) Under the BRM, we discuss the implementation of position based key exchange, which includes p2v key exchange protocols and p2p key exchange protocols.
4) Finally, we compare existing position based key exchange protocols from both security and performance perspectives.
The organization of the rest paper is as follows: Section 2 introduces the p2v mode and the p2p model and gives their security definitions. In Section 3, we present the position based p2v key exchange protocols in one dimension, while Section 4 presents the position based p2p key exchange protocols. We also present extensions of the PbKE protocols in Section 5. Section 6 compares the above protocols in three dimensions. Section 7 concludes our results.
2 The two modes and their security definitions
In this section, we introduce the adversary model, the assumptions used in this paper and the two modes of key exchange in position based cryptography.
2. 1 The adversary model
The colluding adversaries in PbKE protocols have the following capabilities:
1) Adversaries can access all messages (except high min-entropy information in the BRM) when they pass through the wireless communication channel.
2) Adversaries can send any forged message in the wireless communication channel.
3) An adversary can be located at any position except the target position when the prover located in that target position runs a PbKE protocol.
Note that corruption of a prover or a verifier is not considered in position based cryptography. One hand, a prover has no pre-sharing of cryptographic keys, and the unique credential of the prover is its position. the other hand, a secure position based key exchange protocol could not be realized without trusted verifiers.
2. 2 The prover-to-verifier mode
In the p2v mode, a PbKE protocol in d-dimensions consists of a unique prover, some verifiers (at least d+1), and a group of colluding adversaries. At the end of a secure p2v key exchange protocol, the prover located at a valid position can securely share a key with verifiers against the colluding adversaries. For example, the p2v mode of key exchange in 2-dimensions is shown in Fig.1.
Formally, a position based p2v key exchange protocol π in d-dimensional space consists of two algorithms, i. e. π= (Init, Key): the position initialization algorithm Init(P) and the key exchange algorithm Key(V, P, p). There is a set of verifiers V={V 0, V1, …, VD} at positions pos0, pos1, …, posD respectively (D ≤ d). At the same time, there are colluding probabilistic polynomial time adversaries A={A1, A2, …, AK}at positions apos 1, apos 2, …, aposK respectively. The Init(P) algorithm initializes the location of prover P, i. e. if Init(P)=p, this means that the location of P is position p where p is in the tetrahedron enclosed by pos0, pos 1, …, posD. The Key(V, P, p) algorithm against colluding PPT (Probabilistic Polynomial Time) adversaries A={A1, A2, …, AK}establishes a shared secret key sk=Key(V, P, p)between uncorruptedPandVifPis located atp.
Figure1
Figure1
The p2v mode in 2-dimensions
Definition 1 (Position based p2v key exchange) A position based p2v key exchange protocol π is called a secure position based p2v key exchange protocol in security parameter k if for all sets of A ={A1, A 2, …, AK}, given(V, P, p=Init(P)), it is able to distinguish between sk=Key(V, P, p)and a uniform string U(where|U|=|sk|)with a negligible function ε(k). Formally,
2. 3 The prover-to-prover mode
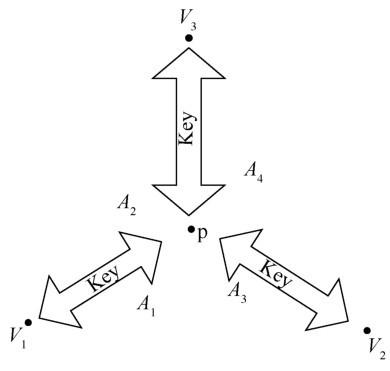
As opposed to the p2v mode, the p2p mode deals with position based key exchange between two provers (with the help of verifiers). Fig.2 shows position based p2p key exchange in two dimensions.
Similar to the p2v mode, a position based p2p key exchange protocol π in d-dimensional space consists of two algorithms, i. e. π= (Init, Key): the position initialization algorithm Init(P) and the key exchange algorithm Key (V, P1, p1, P2, p2). A set of verifiers is denoted by V={V0, V1, …, VD}at positions pos0, pos1, …, posD respectively(D≤d). The colluding probabilistic polynomial time adversaries are denoted by A={A1, A2, …, AK}at positions apos 1, apos2, …, aposK respectively. The Init(P)algorithm can set the location of a prover P as position p where p is in the tetrahedron enclosed by pos0, pos1, …, posD. The Key(V, P1, p1, P2, p2) algorithm against colluding PPT adversaries A={A2, A2, …, AK}could establish a shared secret key sk=Key(V, P1, p1, P2, p2)between uncorrupted P 1 and P2 ifP1 is located atp1 andP2 is located atp2.
Figure2
Figure2
The p2p mode in 2-dimensions
Definition 2 (position based p2p key exchange) A position based prover-to-prover key exchange protocol π is called a secure position based p2p key exchange protocol in security parameter k if for all sets of A={A 1, A2, …, AK}, given (V, P 1, P2, p1 = Init(P1), p2= Init(P2)), it is able to distinguish between sk=Key(V, P 1, p 1, P2, p 2) and a uniform string U(where|U|=|sk|)with a negligible function ε(k). Formally,
2. 4 Assumptions
In this subsection, we present the assumptions used in this paper.
Assumption 1 (The BRM) As in the underlying model in Ref. 4], the protocols in this paper are based on the BRM. The bounded retrieval model assumes that all adversaries can only retrieve part of high minentropy information. More specifically, we have:
1) Verifiers can generate n-bit string X, where X has high min-entropy (δ+β)n.
2) All adversaries can retrieve any part of X when X passes. However, the total retrieved information about X is no more than βn.
Assumption 2 (Private channel) We assume that there is a private channel among all of the verifiers in position based cryptography, i. e. that they can share any message securely.
Assumption 3 (Authenticated broadcast) In this paper, we assume that anyone of the verifiers has an authenticated broadcast channel in this paper. In other words, no adversary can modify or forge a message sent from a verifier in an authenticated channel.
Assumption 4 (DDH assumption) Consider a cyclic group G with prime order q and generator g. If a and b are chosen randomly from Zq, then any PPT adversary A can distinguish between{ga, gb, gab}and{ga, gb, R}with only negligible probability, where R is a uniform string and|R|=|gab|.
In addition, we use BSM PRG (BSM pseudorandom generators)[4]and PRF (pseudorandom function family)[13]to construct the PbKE protocols. Due to space limitations, we omit detailed description of BRM, BSM PRG, PRF and other cryptographic operations.
3 PbKE protocols in the p2v mode
In this section, we first present a position based p2v key exchange protocol in one dimension. Then, we present a generic version of the p2v key exchange protocol p2pKEd in d-dimensions(d∈{1, 2, 3}).
3. 1 Protocol p2vKE1in one dimension
The position based p2v key exchange protocol in one dimension, denoted by p2vKE 1, is shown in Fig.3. For one dimension, we employ two verifiers, denoted by V0 and V1, which send messages at the speed of radio waves.
We assume that the position p being claimed by prover P is located between V0and V1.
Protocol p2vKE1 is secure against an arbitrary number of adversaries colluding to establish a secret key between P and V={V1, V2} as long as the total information that these adversaries can retrieve during the protocol is bounded.
A detailed description of protocol p2vKE1 in the BRM is as follows:
BSM PRG F: {0, 1}n×{0, 1}m→{0, 1}m.
Initialization: Prover P runs the algorithm Init(P) as follows:
(1)Set p=Init(P), i. e. P is located at p.
(2)Set s=(sid, p), where sid is session identity.
Let t(Vi, p)be the time taken for a message from verifier Vi to reach position p.
Let T be the time at which the message sent by V0 arrives at p.
Key Exchange: Prover P runs the algorithm Key(V, P, p)as follows:
1) V0generates X0with min-entropy (δ+β)n and m-bit random string r, and V1 generates X1 with minentropy (δ+β)n. V0and V1can share X0, X1and r over a private channel.
2) V 0 computes y1 = F(X1, r), sk = F(X 0, y 1). V 0 sends (X0, r, s) at time T-t(V0, p) over an authenticated broadcast channel.
3)V1 also computes y 1=F(X 1, r), sk=F(X 0, y 1)and sends (X1, s) at time T-t(V1, p) over an authenticated broadcast channel.
4) Upon receiving (X0, r, s) and (X1, s) at time T, P first computes y1=F(X1, r). Then, P computes sk=F(X0, y1)as a shared key.
Theorem 1 If F is an ε-secure BSM PRG, X0and X1 have min-entropy (δ+β)n and βn is the total retrieval bound, then protocol p2vKE1 is a secure position based p2v key exchange protocol in one dimension against an arbitrary number of colluding adversaries.
Outline of proof: Assuming that p2vKE 1 is not secure, we have that adversary G could distinguish between sk generated by Key(V, P, p)and a random string U with a non-negligible probability.
Under the BRM, we know that the adversaries between V1and P can compute only F(X1, r), but that they does not have X0 to compute sk. The adversaries between V2and P cannot compute F(X1, r), thus they cannot compute sk.
According to the Definition of BSM PRG, no adversary could distinguish between sk and U without adequate information. Thus, Theorem 1 holds.
3. 2 Protocol p2vKEdin d-dimensions
Protocol p2vKEd in d-dimensions requires at least(d+1) verifiers to carry out position based p2v key exchange in d-dimensions.
Figure3
Figure3
Protocol p2vKE$lt@span sup=1$gt@1$lt@/span$gt@
The detailed description of protocol p2vKEd in the BRM is as follows:
BSM PRG F: {0, 1}n×{0, 1}m→{0, 1}m.
Initialization: The Initialization phase is as same as that of protocol p2vKE 1.
Key Exchange:
1) V0generates X0with min-entropy (δ+β)n and m-bit random string r, and Vi generates X i with minentropy(δ+β)n(1≤i≤d). Vi can share X 0, {X i}(1≤i≤d)androver a private channel.
2) V0 computes the shared key sk = F(X0, r0), w h e r e ri-1=F(Xi, ri), rd=r(1≤i≤d). V0 sends(X0, r, s)at time T-t(V0, p) over an authenticated channel, where s=(sid, p).
3) Vi computes the shared key s k and sends (X i, s) at time T-t(Vi, p) over an authenticated channel. (1≤i≤d)
4)Upon receiving(X 0, r, s)and{X1, …, Xd}at time T, P computes the shared key sk=F(X 0, r 0), where ri-1=F(Xi, ri), rd= r (1≤i≤d).
Theorem 2 If F is ε-secure BSM PRG, {Xi} have min-entropy(δ+β)n and βn is the total retrieval bound (0≤i≤d), then protocol p2vKEd is a secure position based p2v key exchange protocol in d-dimensions.
The proof of Theorem 2 is similar to that of Theorem 1. Hence, it will not be discussed in this paper.
With regard to the region available for PbKE in two dimensions or three dimensions, Chandran et al. show that only a very small region near a verifier could not be used to realize secure PbKE, whether it be the p2v mode or the p2p mode[4].
4 PbKE protocols in the p2p mode
In this section, we begin by presenting a position based p2p key exchange protocol in one dimension. Then, we show a generic version of the p2p key exchange protocol p2pKEd in d-dimensions(d∈{1, 2, 3}).
Intuitively, a prover P1could share a key k1with a verifier, and another prover P2could also share a key k2with a verifier using position based p2v key exchange. Then, prover P1and prover P2run a key exchange protocol, such as the Needham-Schroeder protocol[14], involving a trusted third party (i. e. the above verifier) to carry out position based key exchange between prover P1and prover P2. However, a fatal shortcoming of this construction is that the verifier must maintain the correlation between a prover’s current position and its key generated by the p2v mode. Otherwise, a prover may question that whether the position of the other prover during the p2v position based key exchange protocol is its current position or not. Obviously, maintaining this correlation is the construction′s vulnerability and is too costly from the verifiers perspective. Furthermore, this construction demonstrates worse performance in terms of both efficiency and scalability.
Therefore, a construction based on the p2v mode would not be an effective way to realize p2p key exchange. In the following section, we discuss how to realize the position based p2p key exchange protocols.
4. 1 Protocol p2pKE1in one dimension
The position based p2p key exchange protocol in one dimension, denoted by p 2pKE 1, is shown in Fig.4. For one dimension, we employ two verifiers, denoted by V0 and V1(which send messages at the speed of radio waves).
We assume that both position p1and position p2 being claimed by prover P1and prover P2respectively are located between V0and V1.
Protocol p2pKE 1 is secure against an arbitrary number of adversaries, colluding to establish a secret key between P1and P2, as long as the total information that these adversaries can retrieve during the protocol is bounded.
A detailed description of protocol p2pKE1 in the BRM is as follows:
BSM PRG F: {0, 1}n×{0, 1}m→{0, 1}m.
PRF f: {0, 1}2m×{0, 1}l→{0, 1}k.
Initialization: P 1 and P2 run the algorithm Init(P1) and Init(P2)as follows:
1) Set p 1 = Init(P1) and p 2 = Init(P2), i. e. P 1 is located at p1, and P2is located at p2.
2) Set s = (sid, p 1, p 2) where sid is the session identity.
Let t(Vi, p)be the time taken for a message from verifier Vi to reach position p. Let T 1 and T 2 be the times at which the message sent by V0arrive p1and p2respectively. Then, we have that T1-T2=t(V0, p1)-t(V0, p2).
Key exchange: P 1 and P2 run the algorithm Key(V={V1, V2}, P1, p1, P2, p2) as follows:
1) V0generates X0with min-entropy (δ+β)n and m-bit random string r, and V1 generates X1 and X2 with min-entropy (δ+β)n. V0and V1can share X0, X1, X2 androver a private channel.
2) V0computes y1= F(X1, r), z1= F(X0, y1), y2= F(X2, r) and z2= F(X0, y2), and sets
3) V1sends (X1, s) and (X2, s) at time T1-t(V1, p1) and T2-t(V1, p2) respectively over an authenticated broadcast channel.
4) Upon receiving (X0, r, z, s) and (X1, s) at time T1, P1 computes y1=F(X1, r), z1=F(X0, y1)and
5) Upon receiving (X0, r, z, s) and (X2, s) at time T2, P2 computes y2=F(X2, r), z2=F(X0, y2)and
Theorem 3 If F is an ε-secure BSM PRG, f is PRF, Xi has min-entropy (δ+β)n and βn is the total retrieval bound(0≤i≤2), then protocol p2pKE1 is a secure position based p2p key exchange protocol in one dimension against an arbitrary number of colluding adversaries.
Outline of proof: Assuming that p2pKE 1 is not secure, an adversary G can distinguish between sk generated by Key(V, P 1, p 1, P 2, p 2) and a random string U with a non-negligible probability.
Because the messages from the verifiers are broadcasted in an authenticated channel, no adversary can successfully launch an attack on the integrity of those messages. According to the protocol p2pKE1, the session key sk should be equal to f(z 1, z 2). If an adversary G were able to successfully attack the protocol p2pKE1, there are two possible events:
Event 1 Adversary G could distinguish between sk and U without z1and z2. According to the Definition of PRF, Event 1 occurs with only a negligible probability.
Event 2 Adversary G could obtain the value of z1 and z2. According to the BRM, Event 2 occurs with only a negligible probability. We know that the adversaries between V1and P1can compute F(X1, r) and F(X2, r) but do not have X0to compute z1and z2. The adversaries between P1and P2can only compute F(X2, r) but do not have X0 to compute z1. The adversaries between V2and P2cannot compute F(X1, r) and F(X2, r), thus they cannot obtain z1and z2.
Figure4
Figure4
Protocol p2pKE1
Therefore, if f is a PRF and F is an ε-secure BSM PRG, then εf, εF1, εF2, εF3, and εF4 are negligible, and εG is also negligible. Theorem 3 holds.
4. 2 Protocol p2pKEdin d-dimensions
Protocol p2pKEd in d dimensions requires at least (d+1) verifiers to realize position based p2p key exchange in d-dimensions.
A detailed description of protocol p2pKEd in the BRM is as follows:
BSM PRG F: {0, 1}n×{0, 1}m→{0, 1}m.
PRF f: {0, 1}2m×{0, 1}l→{0, 1}k.
Initialization is the same as that of protocol p 2 pKE 1. Key exchange:
1) V0generates X0with min-entropy (δ+β)n and m-bit random string r, and Vi generates X(i, 1)and X(i, 2) with min-entropy(δ+β)n(1≤i≤d). Vi can share X 0, {X(i, j)} (1≤i≤d, 1≤j≤2) and r over a private channel.
2) V0computes z1= F(X0, r(0, 1)) and z2=F(X0, r(0, 2)), where r(i-1, j)= F(X(i, j), r(i, j)), r(d, j)= r (1≤i≤d, 1≤j ≤ 2), and sets
3) Vi sends (X(i, 1), s) and (X(i, 2), s) at time T 1-t(Vi, p 1)and T 2-t(Vi, p 2)respectively over an authenticated channel. (1≤i≤d)
4) Upon receiving (X0, r, z, s) and {X(1, 1), … , X(d, 1)}at time T1, P1computes z1= F(X0, r(0, 1)) where r(i-1, 1)=F(X(i, 1), r(i, 1)), r(d, 1)=r(1≤i≤d)and
5) Upon receiving (X0, r, z, s) and {X(1, 2), …, X(d, 2)}at time T2, P2computes z2= F(X0, r(0, 2)) where r(i-1, 2)=F(X(i, 2), r(i, 2)), r(d, 2)=r(1≤i≤d)and
Theorem 4 If F is an ε-secure BSM PRG, f is a PRF, X0 and {X(i, j)} have min-entropy (δ+β)n andβn is the total retrieval bound (1≤i≤d, 1≤j≤2), then protocol p2 pKEd is a secure p2p position based key exchange protocol in d-dimensions.
The proof of Theorem 4 is omitted due to space limitations.
5 Extensions
In this section, we extend the above protocols in order to establish some useful properties of key exchange, including key confirmation and without key escrow. Due to space limitations, we omit the detailed descriptions and security proofs of the extended protocols.
5. 1 Protocols with key confirmation
A key exchange protocol between parties A and B satisfies mutual key confirmation if both of them are assured that the other party possesses the secret key. Obviously, protocol p2vKEd and p2pKEd do not have the key confirmation property. That is, a prover has no assurance that whether the verifiers (in the p2v mode) or the other prover (in the p2p mode) can obtain the shared key or not.
We can use message authentication code (MAC) to extend PbKE protocols for the key confirmation property as follows.
Assuming that g is a secure MAC algorithm, and f is a secure PRF, the prover P and the verifier Vi(in the p2v mode) or the other prover P′(in the p2p mode) have shared the secret key sk. First, the prover P and the verifier Vi(in the p2v mode)or the other prover P′(in the p2p mode)can compute the encryption key ek=f(sk, 0)and the authentication key ak=f(sk, 1) as a MAC key. Second, the prover P can compute c1=g(a k, (P, s, r)), and either the verifier Vi(in the p2v mode)can compute c 2=g(a k, (Vi, s, r))or the other prover P′(in the p2p mode) can compute c2 = g(ak, (P′, s, r)). Finally, they exchange the MAC values c1 and c2, and verify the validity of the MAC value from the other party. If both of the MAC values pass the verification, they can confirm that the other party must hold the same key.
5. 2 Protocols without key escrow
In the above protocols, we assume that all of the verifiers are trusted. According to the logic of p2 pKEd (or p2pKECd), all verifiers can compute the shared key between provers P1and prover P2in the p2p mode, which implies the problem of key escrow[15].
However, in some applications, there are only semi-trusted verifiers that provide the positionrelated services. Therefore, prover P1and prover P2 maybe wish to keep their communication confidential from the semi-trusted verifiers in the p2p mode. In fact, a semi-trusted verifier can be treated as a passive attacker in the p2p mode.
Based on the DDH (Decision Diffie-Hellman) assumption[16], we construct a position based p2p key exchange protocol p 2pKEEd without key escrow by adding a DH Exchange phase.
The protocol p2pKEEd is shown as follows:
BSM PRG F: {0, 1}n×{0, 1}m→{0, 1}m.
PRF f: {0, 1}2m×{0, 1}l→{0, 1}k.
MAC g : {0, 1}l×{0, 1}2m→{0, 1}k.
G: a cyclic group with prime orderqand generatorg. Initialization & Key Exchange: Prover P1and prover P2run the Initialization and Key Exchange phases as in protocol p2pKEd and share a secret sk.
DH Exchange:
1)P 1 selects a random a from Zq, and sends(P1, s, ga)to P2.
2)Upon receiving(P1, s, ga), P2 selects a random b from Zq, computes key=(ga)b and the authentication tag c2=g(sk, (P2, s, gb, ga)), then it sends(P2, s, gb, c2) to P1.
3)Upon receiving(P2, s, gb, c 2), P 1 first verifies the validity of the authentication tag c2, and if successful computes key=(gb)a and the authentication tag c1=g(sk, (P1, s, ga, gb)). Then, P1 sends(P 1, s, c 1)to P2 and outputs key as a shared key.
4) Upon receiving (P1, s, c1), P2verifies the validity of c1. If successful, P2outputs key as a shared key.
Obviously, protocol p2 pKEEd, like protocol p2pKECd, has the property of key confirmation when using the message authentication code g(sk, •). At the same time, p2pKEEd is also a secure position based p2p key exchange protocol if the DDH assumption holds.
6 Comparisons
In this section, we compare the PbKE protocols in three dimensions. Table1 shows the comparison results.
Security: It is obvious that all of the position based key exchange protocols in this paper satisfy the Definition of a secure position based key exchange under Assumption 1, Assumption 2 and Assumption 3.
In addition, protocol p2vKEC3 and p2pKEC3 have the property of key confirmation, while protocol p2pKEE3 has the properties of key confirmation and being without key escrow by using Assumption 4 (i. e. the DDH assumption).
Performance: From the viewpoint of the verifiers in the p2p mode, the communication overhead and computation cost are the same. In other words, protocol p2pKEC3 and protocol p2pKEE3 would not generate additional cost for the verifiers, which helps the verifiers to provide reliable position-related services.
Protocols p 2vKE3 and p2 pKE3 are suitable for energy-limited applications, since the provers in protocol p2vKE3 and p2pKE 3 have no communication overhead.
Compared to protocol p2vKE3 and p2pKE3, protocol p2vKEC3 and p2pKEC3 incur extra communication overhead and computational cost to the prover for the key confirmation property. We note that the added operation cost of PRF or MAC is acceptable since there are some very efficient implementations of PRF and MAC for lowpower devices.
Note that position based cryptographic protocols using the TOA technique have a disadvantage in that they are not robust to round trip delays, which include propagation delays and processing delays. Therefore, the PbKE protocols in this paper as well as the protocols in Ref. [4] are all based on an assumption that there is no round trip delay: that is that all the participants can immediately send, receive and process data without delay.
7 Conclusion and future work
Position based key exchange is a basic primitive in position based cryptography. This paper distinguishes the prover-to-verifier mode and the prover-toprover mode of position based key exchange. According to the different requirements of the two modes, this paper discusses the security definitions and the implementation of position based key exchange. Moreover, this paper extends position based key exchange protocols in order to capture two meaningful properties of key exchange: key confirmation and without key escrow. Finally, this paper compares the position based key exchange protocols in two modes from both security and performance perspectives.
The next step will be to find new assumptions for position based cryptography and to construct new position based key exchange protocols that are more robust to round trip delays.
Table1 Comparison results
| protocol | p2vKE3 | p2vKEC3 | p2pKE3 | p2pKEC3 | p2pKEE3 |
| verifier computation | 4F | 4F + 2F+2g | 8F | 8F | 8F |
| verifier communication | |r|+4|X| | |r|+4|X|+|g| | |r|+ 7|X| | |r|+7|X| | |r|+7|X| |
| prover computation | 4F | 4F+2f+2g | 4F+f | 4F + 3f + 2g | 4F+ f + 2g + 2E |
| prover communication | 0 | |g| | 0 | |g| | |g| + |q| |
| mode | p2v | p2v | p2p | p2p | p2p |
| set-up assumptions | 1,2,3 | 1,2,3 | 1,2,3 | 1,2,3 | 1,2,3,4 |
| key confirmation | no | yes | no | yes | yes |
| without key escrow | — | — | no | no | yes |
In Tab.1, f denotes the cost of one operation of PRF; g denotes the cost of one computation or verification of MAC; F denotes the cost of one operation of BSM PRG; E denotes the cost of one exponential operation in the DH exchange.
Reference
Evolution of mobile location-based services
[J].
Location privacy in pervasive computing
[J].
Universally composable secure TNC model and EAP-TNC protocol in IF-T
[J].
Position based cryptography
[C]//
Position-based quantum cryptography: impossibility and constructions
[J].
Insecurity of position-based quantumcryptography protocols against entanglement attacks
[J]. Physical review a,2011,83(1): 012322.
One-sided device-independent QKD and position-based cryptography from monogamy games
[C]//
Universally composable secure positioning in the bounded retrieval model
[J].
UC security model of position based key exchange
[J].
Provably secure position based prover-to-prover key exchange protocols
[J].
SPINS: security protocols for sensor networks
[J].
Universally composable onetime signature and broadcast authentication
[J].
How to construct random functions
[J].
Protocol derivation system for the Needham-Schroeder family
[J].
Identity based authenticated key agreement protocols from pairings
[J].
The decision Diffie-Hellman problem
[J].