Searchable symmetric encryption: improved definitions and efficient constructions
3
2016
... In a searchable encryption scheme, the security of the documents and keywords stored on the server should be guaranteed. In addition, the security of query keywords should also be assured. Moreover, the following two security items should also be protected[1]: ...
... A searchable symmetric encryption scheme should satisfy various security requirements. The privacy of documents, search index, and query keywords should be protected, as well as the search pattern and access pattern. Song, et al. [2]argued that their scheme is provably secure because the server cannot learn any information about the plaintext by knowing the ciphertext. However, this kind of security is not strong enough in the context of SSE. IND1-CKA and the stronger IND2-CKA security model, which address the security of keyword indexes, have been proposed by Goh[3]. In both security models, an adversary A cannot learn the contents of a document from its index. In the IND1-CKA model, it is assumed that the indexes are built from documents with the same number of keywords. Conversely, in the IND2-CKA model, this assumption is not necessary. However these two models do not consider the security of trapdoors. Curtmola, et al. [1]introduced new adversarial models that consider the security of trapdoors. The first is a non-adaptive model, IND-CKA1, in which the adversary does not consider the trapdoors and search results of previous searches when he or she chooses challenge search queries. The other is an adaptive model, IND-CKA2, in which the adversary chooses their challenge search queries with the knowledge of trapdoors and search results previously obtained. In this article, we primarily focus on the IND-CKA1 and IND-CKA2 security models to compare various schemes. ...
... Keyword-based Index: Another kind of secure index, called a keyword-based secure index, was proposed by Curtmola, et al. [1]. In this keyword-based secure index, one keyword corresponds to many document identifiers. In this scheme, the search time for a query keyword is linear in the number of documents containing the query keyword. Consequently, compared with the document-based index, keyword-based index is more efficient in searching a query. However, updating a keyword-based index when documents are added, deleted, or modified in the collection is difficult. ...
Practical techniques for searches on encrypted data
3
2000
... A searchable symmetric encryption scheme should satisfy various security requirements. The privacy of documents, search index, and query keywords should be protected, as well as the search pattern and access pattern. Song, et al. [2]argued that their scheme is provably secure because the server cannot learn any information about the plaintext by knowing the ciphertext. However, this kind of security is not strong enough in the context of SSE. IND1-CKA and the stronger IND2-CKA security model, which address the security of keyword indexes, have been proposed by Goh[3]. In both security models, an adversary A cannot learn the contents of a document from its index. In the IND1-CKA model, it is assumed that the indexes are built from documents with the same number of keywords. Conversely, in the IND2-CKA model, this assumption is not necessary. However these two models do not consider the security of trapdoors. Curtmola, et al. [1]introduced new adversarial models that consider the security of trapdoors. The first is a non-adaptive model, IND-CKA1, in which the adversary does not consider the trapdoors and search results of previous searches when he or she chooses challenge search queries. The other is an adaptive model, IND-CKA2, in which the adversary chooses their challenge search queries with the knowledge of trapdoors and search results previously obtained. In this article, we primarily focus on the IND-CKA1 and IND-CKA2 security models to compare various schemes. ...
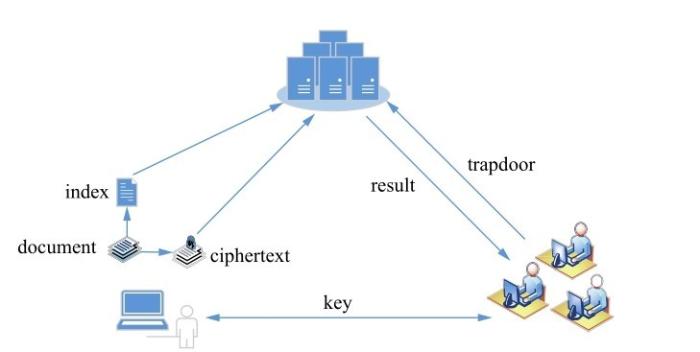
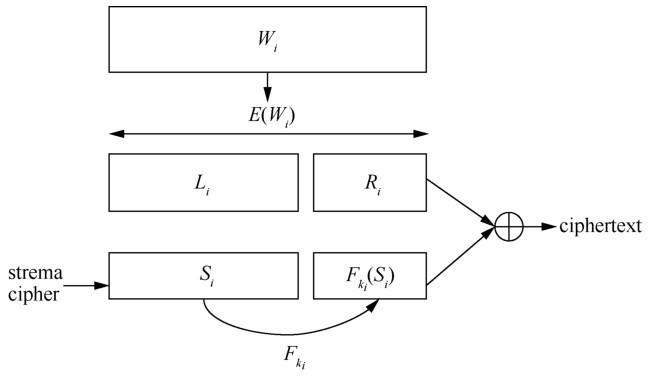
... 1) SSE schemes with sequential scan. Song, et al. [2] proposed the first SSE scheme. In their solution, search is performed by sequentially scanning the entire ciphertext. The underlying idea of this scheme is that the ciphertext is obtained by XORing each of the keywords in the plaintext with a sequence of pseudorandom bits. Thus, it is allowed to directly search on the ciphertext. ...
... Unlike the scheme proposed by Song, et al. [2], this scheme is based on a secure index. The advantage of this scheme is that the server only needs to search over the search indexes instead of scanning the entire ciphertext. As a result, the search efficiency is improved. However, the server also has to search each index and the search work for a query is linear in the number of documents, even if only one document contains the query keyword. We denote this kind of secure index as document-based index, in which the index corresponds with the documents. ...
Secure indexes
2
2003
... A searchable symmetric encryption scheme should satisfy various security requirements. The privacy of documents, search index, and query keywords should be protected, as well as the search pattern and access pattern. Song, et al. [2]argued that their scheme is provably secure because the server cannot learn any information about the plaintext by knowing the ciphertext. However, this kind of security is not strong enough in the context of SSE. IND1-CKA and the stronger IND2-CKA security model, which address the security of keyword indexes, have been proposed by Goh[3]. In both security models, an adversary A cannot learn the contents of a document from its index. In the IND1-CKA model, it is assumed that the indexes are built from documents with the same number of keywords. Conversely, in the IND2-CKA model, this assumption is not necessary. However these two models do not consider the security of trapdoors. Curtmola, et al. [1]introduced new adversarial models that consider the security of trapdoors. The first is a non-adaptive model, IND-CKA1, in which the adversary does not consider the trapdoors and search results of previous searches when he or she chooses challenge search queries. The other is an adaptive model, IND-CKA2, in which the adversary chooses their challenge search queries with the knowledge of trapdoors and search results previously obtained. In this article, we primarily focus on the IND-CKA1 and IND-CKA2 security models to compare various schemes. ...
... 2) SSE schemes with secure index. Document-based Index: To improve search efficiency, Goh[3]proposed a secure index construction using pseudorandom functions and Bloom filters[4]. With a Bloom filter, one can quickly determine whether an element belongs to a set. In this scheme, the pseudorandom function is applied twice to each keyword in the document. Then, the outputs are mapped to the Bloom filter. With the knowledge of the Bloom filter, it is much easier to determine whether a document contains a certain keyword. ...
Space/time trade-offs in hash coding with allowable errors
1
1970
... 2) SSE schemes with secure index. Document-based Index: To improve search efficiency, Goh[3]proposed a secure index construction using pseudorandom functions and Bloom filters[4]. With a Bloom filter, one can quickly determine whether an element belongs to a set. In this scheme, the pseudorandom function is applied twice to each keyword in the document. Then, the outputs are mapped to the Bloom filter. With the knowledge of the Bloom filter, it is much easier to determine whether a document contains a certain keyword. ...
Computationally efficient searchable symmetric encryption
1
2010
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Dynamic searchable symmetric encryption
1
2012
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Parallel and dynamic searchable symmetric encryption
1
2013
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Practical dynamic searchable encryption with small leakage
1
2014
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Dynamic searchable encryption in very-large databases:data structures and implementation
1
2014
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Dynamic searchable encryption via blind storage
1
2014
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Searchable encryption with secure and efficient updates
1
2014
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Dynamic symmetric searchable encryption from constrained functional encryption
1
2016
... 3) Dynamic SSE scheme. Van Liesdonk, et al. [5] proposed a dynamic SSE scheme that can deal with document updates. In their scheme, the search time is logarithmic in the keywords stored in the server. The basic scheme extends to two schemes, both of which support document updates. The first scheme is interactive, whereas the second is no interactive. Kamara, et al. [6]proposed an extension of Curtmola, et al. 's scheme to support updates, which is based on PRFs and XORs. However, updates would leak some information about the trapdoors. Subsequently, Kamara and Papamanthou[7]proposed a new dynamic tree based SSE scheme. In their proposed scheme, no information is leaked after the updating operation. Stefanov, et al. [8]proposed an efficient dynamic SSE scheme with a small information leakage. Various researchers have also focused on the dynamic property[9, , [10,11,12]. A comparison of several classic SSE schemes is given in Tab.1. In the table, n denotes the size of the documents set, r denotes the number of documents containing query keyword ω, m denotes the size of the keywords space and p denotes the number of cores. ...
Leakage-abuse attacks against searchable encryption
1
2015
... Cash, et al. [13]and Zhang, et al. [14]recently focused on attacks on the SSE scheme, whereas Ishai, et al. [15] focused on improving its security. Further, Kamara and Moataz[16]focused on improving its functionality, while Asharov, et al. [17]focused on improving its performance. ...
All your queries are belong to us: the power of file-injection attacks on searchable encryption
1
2016
... Cash, et al. [13]and Zhang, et al. [14]recently focused on attacks on the SSE scheme, whereas Ishai, et al. [15] focused on improving its security. Further, Kamara and Moataz[16]focused on improving its functionality, while Asharov, et al. [17]focused on improving its performance. ...
Private large-scale databases with distributed searchable symmetric encryption
1
2016
... Cash, et al. [13]and Zhang, et al. [14]recently focused on attacks on the SSE scheme, whereas Ishai, et al. [15] focused on improving its security. Further, Kamara and Moataz[16]focused on improving its functionality, while Asharov, et al. [17]focused on improving its performance. ...
SQL on structurally-encrypted databases
1
2016
... Cash, et al. [13]and Zhang, et al. [14]recently focused on attacks on the SSE scheme, whereas Ishai, et al. [15] focused on improving its security. Further, Kamara and Moataz[16]focused on improving its functionality, while Asharov, et al. [17]focused on improving its performance. ...
Searchable symmetric encryption: optimal locality in linear space via two-dimensional balanced allocations
1
2016
... Cash, et al. [13]and Zhang, et al. [14]recently focused on attacks on the SSE scheme, whereas Ishai, et al. [15] focused on improving its security. Further, Kamara and Moataz[16]focused on improving its functionality, while Asharov, et al. [17]focused on improving its performance. ...
Fuzzy keyword search over encrypted data in cloud computing
1
2010
... 3. 3. 2 Fuzzy keyword search In the SSE scheme, a user submits the trapdoor of a query keyword to the server, and the server returns the documents containing the query keyword. However, if the query keyword does not match a preset keyword, such as “campus” and “compus”, the keyword search will fail. Fortunately, fuzzy keyword search can deal with this problem as it can tolerate minor typos and formatting inconsistencies. Li, et al. [18]constructed a fuzzy keywords collection using “edit distance” to quantify keywords similarity. Kuzu, et al. [19]used gram to construct fuzzy sets and LSH and Bloom filter to construct a ranking search scheme. Because a semi-honest server may only return a fraction of the results, Wang[20]proposed a verifiable fuzzy keyword search scheme that not only supports fuzzy keyword search, but also provides proof to verify whether the server returns all the search results. Several other proposed schemes also support fuzzy keyword search[21,22]. ...
Efficient similarity search over encrypted data
1
2012
... 3. 3. 2 Fuzzy keyword search In the SSE scheme, a user submits the trapdoor of a query keyword to the server, and the server returns the documents containing the query keyword. However, if the query keyword does not match a preset keyword, such as “campus” and “compus”, the keyword search will fail. Fortunately, fuzzy keyword search can deal with this problem as it can tolerate minor typos and formatting inconsistencies. Li, et al. [18]constructed a fuzzy keywords collection using “edit distance” to quantify keywords similarity. Kuzu, et al. [19]used gram to construct fuzzy sets and LSH and Bloom filter to construct a ranking search scheme. Because a semi-honest server may only return a fraction of the results, Wang[20]proposed a verifiable fuzzy keyword search scheme that not only supports fuzzy keyword search, but also provides proof to verify whether the server returns all the search results. Several other proposed schemes also support fuzzy keyword search[21,22]. ...
Efficient verifiable fuzzy keyword search over encrypted data in cloud computing
1
2013
... 3. 3. 2 Fuzzy keyword search In the SSE scheme, a user submits the trapdoor of a query keyword to the server, and the server returns the documents containing the query keyword. However, if the query keyword does not match a preset keyword, such as “campus” and “compus”, the keyword search will fail. Fortunately, fuzzy keyword search can deal with this problem as it can tolerate minor typos and formatting inconsistencies. Li, et al. [18]constructed a fuzzy keywords collection using “edit distance” to quantify keywords similarity. Kuzu, et al. [19]used gram to construct fuzzy sets and LSH and Bloom filter to construct a ranking search scheme. Because a semi-honest server may only return a fraction of the results, Wang[20]proposed a verifiable fuzzy keyword search scheme that not only supports fuzzy keyword search, but also provides proof to verify whether the server returns all the search results. Several other proposed schemes also support fuzzy keyword search[21,22]. ...
Biometric identification over encrypted data made feasible
1
2009
... 3. 3. 2 Fuzzy keyword search In the SSE scheme, a user submits the trapdoor of a query keyword to the server, and the server returns the documents containing the query keyword. However, if the query keyword does not match a preset keyword, such as “campus” and “compus”, the keyword search will fail. Fortunately, fuzzy keyword search can deal with this problem as it can tolerate minor typos and formatting inconsistencies. Li, et al. [18]constructed a fuzzy keywords collection using “edit distance” to quantify keywords similarity. Kuzu, et al. [19]used gram to construct fuzzy sets and LSH and Bloom filter to construct a ranking search scheme. Because a semi-honest server may only return a fraction of the results, Wang[20]proposed a verifiable fuzzy keyword search scheme that not only supports fuzzy keyword search, but also provides proof to verify whether the server returns all the search results. Several other proposed schemes also support fuzzy keyword search[21,22]. ...
Achieving usable and privacyassured similarity search over outsourced cloud data
1
2012
... 3. 3. 2 Fuzzy keyword search In the SSE scheme, a user submits the trapdoor of a query keyword to the server, and the server returns the documents containing the query keyword. However, if the query keyword does not match a preset keyword, such as “campus” and “compus”, the keyword search will fail. Fortunately, fuzzy keyword search can deal with this problem as it can tolerate minor typos and formatting inconsistencies. Li, et al. [18]constructed a fuzzy keywords collection using “edit distance” to quantify keywords similarity. Kuzu, et al. [19]used gram to construct fuzzy sets and LSH and Bloom filter to construct a ranking search scheme. Because a semi-honest server may only return a fraction of the results, Wang[20]proposed a verifiable fuzzy keyword search scheme that not only supports fuzzy keyword search, but also provides proof to verify whether the server returns all the search results. Several other proposed schemes also support fuzzy keyword search[21,22]. ...
Secure conjunctive keyword search over encrypted data
1
2004
... 3. 3. 3 Conjunctive keyword search Conjunctive keyword search allows a user to obtain documents containing several keywords during a single query. It is more efficient and suitable for real applications than single keyword search. A trivial procedure is to perform single keyword search for each keyword separately and then deal with the results. However, it is inefficient and leaks some information to the server. Golle, et al. [23]proposed the first two conjunctive keyword search schemes. The communication cost of their first scheme is linear in the number of documents, but the major job can be done offline. Their second scheme requires only constant communication and there is no need to do anything offline. Ballard, et al. [24]presented two conjunctive keyword search constructions, one based on the nonstandard shamir secret sharing technique and the other on bilinear pairings. However, in their case, the trapdoor size is linear in the number of documents being searched. Cash, et al. [25]extended conjunctive query to Boolean query. Faber, et al. [26] extended Cash, et al. ′s scheme[25]to support range, substring, wildcard, and phrase queries. In their system, the least frequent keyword is queried first, and the search results are then applied to other keywords. Theirs is the first sublinear SSE construction supporting Boolean query. Several other studies have also been conducted on this topic[27,28]. ...
Achieving e_cient conjunctive keyword searches over encrypted data
1
2005
... 3. 3. 3 Conjunctive keyword search Conjunctive keyword search allows a user to obtain documents containing several keywords during a single query. It is more efficient and suitable for real applications than single keyword search. A trivial procedure is to perform single keyword search for each keyword separately and then deal with the results. However, it is inefficient and leaks some information to the server. Golle, et al. [23]proposed the first two conjunctive keyword search schemes. The communication cost of their first scheme is linear in the number of documents, but the major job can be done offline. Their second scheme requires only constant communication and there is no need to do anything offline. Ballard, et al. [24]presented two conjunctive keyword search constructions, one based on the nonstandard shamir secret sharing technique and the other on bilinear pairings. However, in their case, the trapdoor size is linear in the number of documents being searched. Cash, et al. [25]extended conjunctive query to Boolean query. Faber, et al. [26] extended Cash, et al. ′s scheme[25]to support range, substring, wildcard, and phrase queries. In their system, the least frequent keyword is queried first, and the search results are then applied to other keywords. Theirs is the first sublinear SSE construction supporting Boolean query. Several other studies have also been conducted on this topic[27,28]. ...
Highly-scalable searchable symmetric encryption with support for Boolean queries
2
2013
... 3. 3. 3 Conjunctive keyword search Conjunctive keyword search allows a user to obtain documents containing several keywords during a single query. It is more efficient and suitable for real applications than single keyword search. A trivial procedure is to perform single keyword search for each keyword separately and then deal with the results. However, it is inefficient and leaks some information to the server. Golle, et al. [23]proposed the first two conjunctive keyword search schemes. The communication cost of their first scheme is linear in the number of documents, but the major job can be done offline. Their second scheme requires only constant communication and there is no need to do anything offline. Ballard, et al. [24]presented two conjunctive keyword search constructions, one based on the nonstandard shamir secret sharing technique and the other on bilinear pairings. However, in their case, the trapdoor size is linear in the number of documents being searched. Cash, et al. [25]extended conjunctive query to Boolean query. Faber, et al. [26] extended Cash, et al. ′s scheme[25]to support range, substring, wildcard, and phrase queries. In their system, the least frequent keyword is queried first, and the search results are then applied to other keywords. Theirs is the first sublinear SSE construction supporting Boolean query. Several other studies have also been conducted on this topic[27,28]. ...
... [25]to support range, substring, wildcard, and phrase queries. In their system, the least frequent keyword is queried first, and the search results are then applied to other keywords. Theirs is the first sublinear SSE construction supporting Boolean query. Several other studies have also been conducted on this topic[27,28]. ...
Rich queries on encrypted data: beyond exact matches
1
2015
... 3. 3. 3 Conjunctive keyword search Conjunctive keyword search allows a user to obtain documents containing several keywords during a single query. It is more efficient and suitable for real applications than single keyword search. A trivial procedure is to perform single keyword search for each keyword separately and then deal with the results. However, it is inefficient and leaks some information to the server. Golle, et al. [23]proposed the first two conjunctive keyword search schemes. The communication cost of their first scheme is linear in the number of documents, but the major job can be done offline. Their second scheme requires only constant communication and there is no need to do anything offline. Ballard, et al. [24]presented two conjunctive keyword search constructions, one based on the nonstandard shamir secret sharing technique and the other on bilinear pairings. However, in their case, the trapdoor size is linear in the number of documents being searched. Cash, et al. [25]extended conjunctive query to Boolean query. Faber, et al. [26] extended Cash, et al. ′s scheme[25]to support range, substring, wildcard, and phrase queries. In their system, the least frequent keyword is queried first, and the search results are then applied to other keywords. Theirs is the first sublinear SSE construction supporting Boolean query. Several other studies have also been conducted on this topic[27,28]. ...
Efficient conjunctive keyword search on encrypted data storage system
1
2006
... 3. 3. 3 Conjunctive keyword search Conjunctive keyword search allows a user to obtain documents containing several keywords during a single query. It is more efficient and suitable for real applications than single keyword search. A trivial procedure is to perform single keyword search for each keyword separately and then deal with the results. However, it is inefficient and leaks some information to the server. Golle, et al. [23]proposed the first two conjunctive keyword search schemes. The communication cost of their first scheme is linear in the number of documents, but the major job can be done offline. Their second scheme requires only constant communication and there is no need to do anything offline. Ballard, et al. [24]presented two conjunctive keyword search constructions, one based on the nonstandard shamir secret sharing technique and the other on bilinear pairings. However, in their case, the trapdoor size is linear in the number of documents being searched. Cash, et al. [25]extended conjunctive query to Boolean query. Faber, et al. [26] extended Cash, et al. ′s scheme[25]to support range, substring, wildcard, and phrase queries. In their system, the least frequent keyword is queried first, and the search results are then applied to other keywords. Theirs is the first sublinear SSE construction supporting Boolean query. Several other studies have also been conducted on this topic[27,28]. ...
Keyword field-free conjunctive keyword searches on encrypted data and extension for dynamic groups
1
2008
... 3. 3. 3 Conjunctive keyword search Conjunctive keyword search allows a user to obtain documents containing several keywords during a single query. It is more efficient and suitable for real applications than single keyword search. A trivial procedure is to perform single keyword search for each keyword separately and then deal with the results. However, it is inefficient and leaks some information to the server. Golle, et al. [23]proposed the first two conjunctive keyword search schemes. The communication cost of their first scheme is linear in the number of documents, but the major job can be done offline. Their second scheme requires only constant communication and there is no need to do anything offline. Ballard, et al. [24]presented two conjunctive keyword search constructions, one based on the nonstandard shamir secret sharing technique and the other on bilinear pairings. However, in their case, the trapdoor size is linear in the number of documents being searched. Cash, et al. [25]extended conjunctive query to Boolean query. Faber, et al. [26] extended Cash, et al. ′s scheme[25]to support range, substring, wildcard, and phrase queries. In their system, the least frequent keyword is queried first, and the search results are then applied to other keywords. Theirs is the first sublinear SSE construction supporting Boolean query. Several other studies have also been conducted on this topic[27,28]. ...
Confidentialitypreserving rank-ordered search
1
2007
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Zerber+ r: Top-k retrieval from a confidential index
1
2009
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Secure ranked keyword search over encrypted cloud data
1
2010
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Enabling secure and efficient ranked keyword search over outsourced cloud data
1
2012
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Privacy preserving multi-keyword ranked search over encrypted cloud data
1
2011
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Verifiable privacy-preserving multi-keyword text search in the cloud supporting similarity based ranking
1
2014
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
A secure and dynamic multikeyword ranked search scheme over encrypted cloud data
1
2016
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
An efficient privacy-preserving ranked keyword search method
1
2016
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
A practical and secure multi-keyword search method over encrypted cloud data
1
2013
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Secure ranked multi-keyword search for multiple data owners in cloud computing
1
2014
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Parallel search over encrypted data under attribute based encryption on the Cloud Computing
1
2015
... 3. 3. 4 Ranked and verifiable keyword search Ranked keyword search can optimize search results by returning the most relevant documents. This can reduce network traffic and enhance system usability. Swaminathan, et al. [29], Zerr, et al. [30], and Wang, et al. [31,32]achieved ranked search in the single keyword search paradigm using an order-preserving function. Cao, et al. [33]were the first to present a multi-keyword ranked search scheme with“coordinate matching”measurement. However, their search results are ranked based on the number of matching keywords without considering the importance of Different keywords. Consequently, their results are not very accurate. Sun, et al. [34]proposed a multi-keyword ranked search scheme using“cosine measure”techniques. Their scheme achieves better-than-linear search efficiency at the expense of search accuracy. Xia, et al. [35]recently proposed a dynamic multi-keywords ranked search scheme that uses a secure tree. Chen, et al. [36]proposed a multi-keyword ranked search scheme based on hierarchical clustering index to improve search efficiency. In their scheme, the search time has a linear growth when the size of the data collection has an exponential growth. Other studies have also been conducted on ranked search[37,38,39]. ...
Authenticating query results in edge computing
1
2004
... Verifiable keyword search can detect whether the search results are complete and correct. This can verify inaccurate search results caused by software or hardware failure, storage corruption, or even malicious behavior by a semi-honest server trying to save computation resources. Studies have also been conducted on verifiable keyword search[40,41,42, [43]. However, these studies are based on MHT (Merkle Hash Tree) and signature techniques, which have expensive communication and computation overhead. Chai, et al. [44]proposed a verifiable searchable encryption scheme. Wang, et al. [45]focused on verification of an empty set as a search result. ...
Authenticated index structures for outsourced databases
1
2008
... Verifiable keyword search can detect whether the search results are complete and correct. This can verify inaccurate search results caused by software or hardware failure, storage corruption, or even malicious behavior by a semi-honest server trying to save computation resources. Studies have also been conducted on verifiable keyword search[40,41,42, [43]. However, these studies are based on MHT (Merkle Hash Tree) and signature techniques, which have expensive communication and computation overhead. Chai, et al. [44]proposed a verifiable searchable encryption scheme. Wang, et al. [45]focused on verification of an empty set as a search result. ...
Partially materialized digest scheme: an efficient verification method for outsourced databases
1
2009
... Verifiable keyword search can detect whether the search results are complete and correct. This can verify inaccurate search results caused by software or hardware failure, storage corruption, or even malicious behavior by a semi-honest server trying to save computation resources. Studies have also been conducted on verifiable keyword search[40,41,42, [43]. However, these studies are based on MHT (Merkle Hash Tree) and signature techniques, which have expensive communication and computation overhead. Chai, et al. [44]proposed a verifiable searchable encryption scheme. Wang, et al. [45]focused on verification of an empty set as a search result. ...
UCsecure searchable symmetric encryption
1
2012
... Verifiable keyword search can detect whether the search results are complete and correct. This can verify inaccurate search results caused by software or hardware failure, storage corruption, or even malicious behavior by a semi-honest server trying to save computation resources. Studies have also been conducted on verifiable keyword search[40,41,42, [43]. However, these studies are based on MHT (Merkle Hash Tree) and signature techniques, which have expensive communication and computation overhead. Chai, et al. [44]proposed a verifiable searchable encryption scheme. Wang, et al. [45]focused on verification of an empty set as a search result. ...
Verifiable symmetric searchable encryption for semi-honest but-curious cloud servers
1
2012
... Verifiable keyword search can detect whether the search results are complete and correct. This can verify inaccurate search results caused by software or hardware failure, storage corruption, or even malicious behavior by a semi-honest server trying to save computation resources. Studies have also been conducted on verifiable keyword search[40,41,42, [43]. However, these studies are based on MHT (Merkle Hash Tree) and signature techniques, which have expensive communication and computation overhead. Chai, et al. [44]proposed a verifiable searchable encryption scheme. Wang, et al. [45]focused on verification of an empty set as a search result. ...
Verifiable auditing for outsourced database in cloud computing
1
2015
... Verifiable keyword search can detect whether the search results are complete and correct. This can verify inaccurate search results caused by software or hardware failure, storage corruption, or even malicious behavior by a semi-honest server trying to save computation resources. Studies have also been conducted on verifiable keyword search[40,41,42, [43]. However, these studies are based on MHT (Merkle Hash Tree) and signature techniques, which have expensive communication and computation overhead. Chai, et al. [44]proposed a verifiable searchable encryption scheme. Wang, et al. [45]focused on verification of an empty set as a search result. ...
Public key encryption with keyword search
3
2004
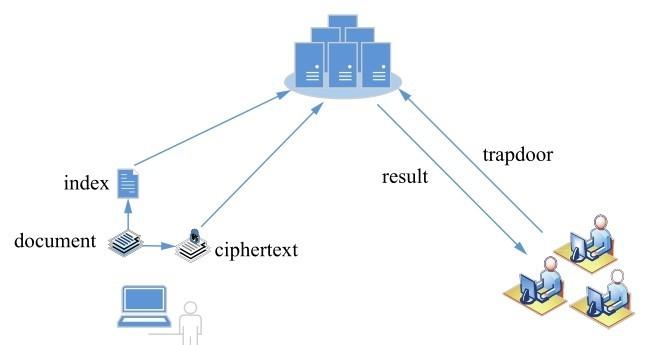
... Consider the following scenario: Bob sends an email with corresponding keywords to Alice. In order to protect the contents of the email and keywords, both are encrypted with Alices public key. However, in this case the email server cannot make a routing decision according to the keywords. Therefore, it is necessary to give the email server the ability to decide whether a certain keyword is contained in an email or not. Meanwhile, the email server cannot learn anything about the contents of the email and keywords. To achieve this goal, Boneh, et al. [46] proposed the first scheme supporting keyword search in a public key system. Fig.3 shows the model of PEKS schemes. ...
... The first PEKS scheme was proposed by Boneh, et al. [46]. It was based on IBE (Identity Based Encryption)[47,48]and consisted of three stages. First, the message sender encrypts her/his message and keywords with the receivers public key in a particular way. The ciphertext is EApub(M), PEKS(Apub, W1), …, PEKS(Apub, Wk), where M is the message content, and Apub is the public key of the receiver. Next, the receiver sends the trapdoor Tω of query keyword W to the server. Finally, the server searches over the ciphertexts and determine whether a certain keyword is in a particular ciphertext. ...
... 2) Secure Channel Free PEKS: Boneh, et al. ’s scheme[46]has the limitation that a secure channel is required to transmit the trapdoors; thus, only the server can learn the trapdoor. However, it is not practical as building a secure channel is expensive. To overcome this problem, Baek, et al. [53]proposed SCF-PEKS (Secure Channel Free PEKS), which does not require a secure channel. This new PEKS scheme adds the servers public/private key pair; hence, only the server can search over the ciphertext. Rhee, et al. [54]subsequently enhanced the security of Beak, et al. ’s model[53]. In their security enhanced model, an attacker can obtain the relationship between ciphertexts and a trapdoor. Recently, Emura, et al. [55]extended the security of the SCF-PEKS scheme to an adaptive SCF-PEKS scheme based on the anonymous IBE. This model allows an attacker to test query keywords adaptively. ...
Identity-based encryption from the Weil pairing
1
2003
... The first PEKS scheme was proposed by Boneh, et al. [46]. It was based on IBE (Identity Based Encryption)[47,48]and consisted of three stages. First, the message sender encrypts her/his message and keywords with the receivers public key in a particular way. The ciphertext is EApub(M), PEKS(Apub, W1), …, PEKS(Apub, Wk), where M is the message content, and Apub is the public key of the receiver. Next, the receiver sends the trapdoor Tω of query keyword W to the server. Finally, the server searches over the ciphertexts and determine whether a certain keyword is in a particular ciphertext. ...
Identity-based cryptosystems and signature schemes
1
1984
... The first PEKS scheme was proposed by Boneh, et al. [46]. It was based on IBE (Identity Based Encryption)[47,48]and consisted of three stages. First, the message sender encrypts her/his message and keywords with the receivers public key in a particular way. The ciphertext is EApub(M), PEKS(Apub, W1), …, PEKS(Apub, Wk), where M is the message content, and Apub is the public key of the receiver. Next, the receiver sends the trapdoor Tω of query keyword W to the server. Finally, the server searches over the ciphertexts and determine whether a certain keyword is in a particular ciphertext. ...
Searchable encryption revisited: consistency properties,relation to anonymous IBE,and extensions
1
2008
... 1) Traditional PEKS: Abdalla, et al. [49]proposed a generic solution for transforming an anonymous IBE scheme into a PEKS scheme. They also constructed a PEKS scheme based on temporary keyword from hierarchical IBE. In their scheme, a trapdoor is produced along with a time interval [s, e], and the mail server is only allowed to test whether a certain keyword w is in the ciphertext during this time interval. This method effectively prevents the server from searching a keyword in the past or future. ...
Public key encryption with searchable keywords based on Jacobi symbols
1
2007
... Di Crescenzo and Saraswat[50]introduced the first PEKS scheme without bilinear maps. Their scheme, transformed from Cocks IBE scheme[51], is based on a variant of the quadratic residuosity problem. The scheme has been proven PK-CKA2 secure in the RO model. However, it has to calculate 4k Jacobi symbols in order to test whether a certain keyword is in a document, where k is a security parameter. Further, the search time is linear in the number of ciphertexts. Moreover, it has a high storage and communication overhead. ...
An identity based encryption scheme based on quadratic residues
1
2001
... Di Crescenzo and Saraswat[50]introduced the first PEKS scheme without bilinear maps. Their scheme, transformed from Cocks IBE scheme[51], is based on a variant of the quadratic residuosity problem. The scheme has been proven PK-CKA2 secure in the RO model. However, it has to calculate 4k Jacobi symbols in order to test whether a certain keyword is in a document, where k is a security parameter. Further, the search time is linear in the number of ciphertexts. Moreover, it has a high storage and communication overhead. ...
Public key encryption with keyword search based on k-resilient IBE
1
2007
... Khader[52]proposed a PEKS scheme based on k-resilient IBE. The scheme is PK-CKA2 secure without an RO model. However, PEKS algorithm is inefficient and involves the calculation of four exponentiations to test whether a certain keyword is in a ciphertext. The scheme was also used to construct another two schemes: one supporting conjunctive keyword search; the other requiring no secure channel to transmit the trapdoors. ...
Public key encryption with keyword search revisited
3
2008
... 2) Secure Channel Free PEKS: Boneh, et al. ’s scheme[46]has the limitation that a secure channel is required to transmit the trapdoors; thus, only the server can learn the trapdoor. However, it is not practical as building a secure channel is expensive. To overcome this problem, Baek, et al. [53]proposed SCF-PEKS (Secure Channel Free PEKS), which does not require a secure channel. This new PEKS scheme adds the servers public/private key pair; hence, only the server can search over the ciphertext. Rhee, et al. [54]subsequently enhanced the security of Beak, et al. ’s model[53]. In their security enhanced model, an attacker can obtain the relationship between ciphertexts and a trapdoor. Recently, Emura, et al. [55]extended the security of the SCF-PEKS scheme to an adaptive SCF-PEKS scheme based on the anonymous IBE. This model allows an attacker to test query keywords adaptively. ...
... [53]. In their security enhanced model, an attacker can obtain the relationship between ciphertexts and a trapdoor. Recently, Emura, et al. [55]extended the security of the SCF-PEKS scheme to an adaptive SCF-PEKS scheme based on the anonymous IBE. This model allows an attacker to test query keywords adaptively. ...
... 3) Against Keyword Guessing Attack: Byun, et al. [56]first raised an off-line KGA (Keyword Guessing Attack) because of the small space for keywords. They also stated that Boneh, et al. ’s scheme is vulnerable to off-line keyword guessing attacks. Yau, et al. [57]asserted that the SCFPEKS[53] and PKE/PEKS[58]schemes are also vulnerable to this attack. They showed that an outside adversary can capture the trapdoor from a public channel (outside KGA), while an inside adversary, such as a malicious server, can capture the trapdoors from either a public or secure channel. Rhee, et al. [59]proposed a scheme against outside KGA that introduces a random variable in the trapdoor computation to make the trapdoors indistinguishable. Fang, et al. [60]proposed a concrete SCF-PEKS against outside KGA. ...
Improved searchable public key encryption with designated tester
1
2009
... 2) Secure Channel Free PEKS: Boneh, et al. ’s scheme[46]has the limitation that a secure channel is required to transmit the trapdoors; thus, only the server can learn the trapdoor. However, it is not practical as building a secure channel is expensive. To overcome this problem, Baek, et al. [53]proposed SCF-PEKS (Secure Channel Free PEKS), which does not require a secure channel. This new PEKS scheme adds the servers public/private key pair; hence, only the server can search over the ciphertext. Rhee, et al. [54]subsequently enhanced the security of Beak, et al. ’s model[53]. In their security enhanced model, an attacker can obtain the relationship between ciphertexts and a trapdoor. Recently, Emura, et al. [55]extended the security of the SCF-PEKS scheme to an adaptive SCF-PEKS scheme based on the anonymous IBE. This model allows an attacker to test query keywords adaptively. ...
Generic constructions of secure channel free searchable encryption with adaptive security
1
2015
... 2) Secure Channel Free PEKS: Boneh, et al. ’s scheme[46]has the limitation that a secure channel is required to transmit the trapdoors; thus, only the server can learn the trapdoor. However, it is not practical as building a secure channel is expensive. To overcome this problem, Baek, et al. [53]proposed SCF-PEKS (Secure Channel Free PEKS), which does not require a secure channel. This new PEKS scheme adds the servers public/private key pair; hence, only the server can search over the ciphertext. Rhee, et al. [54]subsequently enhanced the security of Beak, et al. ’s model[53]. In their security enhanced model, an attacker can obtain the relationship between ciphertexts and a trapdoor. Recently, Emura, et al. [55]extended the security of the SCF-PEKS scheme to an adaptive SCF-PEKS scheme based on the anonymous IBE. This model allows an attacker to test query keywords adaptively. ...
O_-line keyword guessing attacks on recent keyword search schemes over encrypted data
1
2006
... 3) Against Keyword Guessing Attack: Byun, et al. [56]first raised an off-line KGA (Keyword Guessing Attack) because of the small space for keywords. They also stated that Boneh, et al. ’s scheme is vulnerable to off-line keyword guessing attacks. Yau, et al. [57]asserted that the SCFPEKS[53] and PKE/PEKS[58]schemes are also vulnerable to this attack. They showed that an outside adversary can capture the trapdoor from a public channel (outside KGA), while an inside adversary, such as a malicious server, can capture the trapdoors from either a public or secure channel. Rhee, et al. [59]proposed a scheme against outside KGA that introduces a random variable in the trapdoor computation to make the trapdoors indistinguishable. Fang, et al. [60]proposed a concrete SCF-PEKS against outside KGA. ...
O_-line keyword guessing attacks on recent public key encryption with keyword search schemes
1
2008
... 3) Against Keyword Guessing Attack: Byun, et al. [56]first raised an off-line KGA (Keyword Guessing Attack) because of the small space for keywords. They also stated that Boneh, et al. ’s scheme is vulnerable to off-line keyword guessing attacks. Yau, et al. [57]asserted that the SCFPEKS[53] and PKE/PEKS[58]schemes are also vulnerable to this attack. They showed that an outside adversary can capture the trapdoor from a public channel (outside KGA), while an inside adversary, such as a malicious server, can capture the trapdoors from either a public or secure channel. Rhee, et al. [59]proposed a scheme against outside KGA that introduces a random variable in the trapdoor computation to make the trapdoors indistinguishable. Fang, et al. [60]proposed a concrete SCF-PEKS against outside KGA. ...
On the integration of public key data en cryption and public key encryption with keyword search
1
2006
... 3) Against Keyword Guessing Attack: Byun, et al. [56]first raised an off-line KGA (Keyword Guessing Attack) because of the small space for keywords. They also stated that Boneh, et al. ’s scheme is vulnerable to off-line keyword guessing attacks. Yau, et al. [57]asserted that the SCFPEKS[53] and PKE/PEKS[58]schemes are also vulnerable to this attack. They showed that an outside adversary can capture the trapdoor from a public channel (outside KGA), while an inside adversary, such as a malicious server, can capture the trapdoors from either a public or secure channel. Rhee, et al. [59]proposed a scheme against outside KGA that introduces a random variable in the trapdoor computation to make the trapdoors indistinguishable. Fang, et al. [60]proposed a concrete SCF-PEKS against outside KGA. ...
Trapdoor security in a searchable publickey encryption scheme with a designated tester
1
2010
... 3) Against Keyword Guessing Attack: Byun, et al. [56]first raised an off-line KGA (Keyword Guessing Attack) because of the small space for keywords. They also stated that Boneh, et al. ’s scheme is vulnerable to off-line keyword guessing attacks. Yau, et al. [57]asserted that the SCFPEKS[53] and PKE/PEKS[58]schemes are also vulnerable to this attack. They showed that an outside adversary can capture the trapdoor from a public channel (outside KGA), while an inside adversary, such as a malicious server, can capture the trapdoors from either a public or secure channel. Rhee, et al. [59]proposed a scheme against outside KGA that introduces a random variable in the trapdoor computation to make the trapdoors indistinguishable. Fang, et al. [60]proposed a concrete SCF-PEKS against outside KGA. ...
Public key encryption with keyword search secure against keyword guessing attacks without random oracle
1
2013
... 3) Against Keyword Guessing Attack: Byun, et al. [56]first raised an off-line KGA (Keyword Guessing Attack) because of the small space for keywords. They also stated that Boneh, et al. ’s scheme is vulnerable to off-line keyword guessing attacks. Yau, et al. [57]asserted that the SCFPEKS[53] and PKE/PEKS[58]schemes are also vulnerable to this attack. They showed that an outside adversary can capture the trapdoor from a public channel (outside KGA), while an inside adversary, such as a malicious server, can capture the trapdoors from either a public or secure channel. Rhee, et al. [59]proposed a scheme against outside KGA that introduces a random variable in the trapdoor computation to make the trapdoors indistinguishable. Fang, et al. [60]proposed a concrete SCF-PEKS against outside KGA. ...
Constructing PEKS schemes secure against keyword guessing attacks is possible?
1
2009
... For inside KGA, Jeong, et al. [61]showed that constructing a secure and consistent PEKS scheme against KGA is impossible when the number of possible keywords is bounded by some polynomial. Xu, et al. [62]presented a PEKS scheme that supports fuzzy keyword search. In their scheme, more than one keywords share the same fuzzy keyword trapdoor such that the server cannot learn the exact keyword. However, their scheme has limitations in terms of security and efficiency. Chen, et al. [63]proposed a new PEKS framework, called dual-server PEKS, which is secure against inside KGA. ...
Public-key encryption with fuzzy keyword search: a provably secure scheme under keyword guessing attack
1
2013
... For inside KGA, Jeong, et al. [61]showed that constructing a secure and consistent PEKS scheme against KGA is impossible when the number of possible keywords is bounded by some polynomial. Xu, et al. [62]presented a PEKS scheme that supports fuzzy keyword search. In their scheme, more than one keywords share the same fuzzy keyword trapdoor such that the server cannot learn the exact keyword. However, their scheme has limitations in terms of security and efficiency. Chen, et al. [63]proposed a new PEKS framework, called dual-server PEKS, which is secure against inside KGA. ...
Dual-server public-key encryption with keyword search for secure cloud storage
1
2016
... For inside KGA, Jeong, et al. [61]showed that constructing a secure and consistent PEKS scheme against KGA is impossible when the number of possible keywords is bounded by some polynomial. Xu, et al. [62]presented a PEKS scheme that supports fuzzy keyword search. In their scheme, more than one keywords share the same fuzzy keyword trapdoor such that the server cannot learn the exact keyword. However, their scheme has limitations in terms of security and efficiency. Chen, et al. [63]proposed a new PEKS framework, called dual-server PEKS, which is secure against inside KGA. ...
Public key encryption with conjunctive field keyword search
1
2004
... Park, et al. [64]constructed two schemes supporting conjunctive keyword search in public key systems, in which the computation overhead is efficient and trapdoor size is constant. However, the first scheme requires a number of bilinear paring mappings and the number of private keywords is linear in the size of keyword fields. Boneh and Waters[65]presented a public key scheme based on hidden vector encryption that supports comparison queries, subset queries, and arbitrary conjunctive queries. The attribute values cannot be leaked after decryption. However, the ciphertext size is large because of the use of composite order bilinear groups. In addition, it has a high cost in terms of public key size and encryption operation. Fortunately, the decryption key size and decryption cost are minimized. Shi, et al. [66]proposed a scheme supporting multidimensional range query over encrypted data that can be used to share network audit logs. However, it leaks attribute values after decryption. Hwang and Lee[67]improved the size of ciphertext and private key. Kaze, et al. [68]constructed a PEKS scheme supporting disjunctive keyword search that is based on inner-product predicate encryption. However, the ciphertext size and private key size is bounded by some superpolynomial. Lai, et al. [69]introduced an efficient PEKS scheme supporting arbitrary monotone Boolean predicates that is based on key-policy attribute-based encryption (KP-ABE)[70]. ...
Conjunctive,subset,and range queries on encrypted data
1
2007
... Park, et al. [64]constructed two schemes supporting conjunctive keyword search in public key systems, in which the computation overhead is efficient and trapdoor size is constant. However, the first scheme requires a number of bilinear paring mappings and the number of private keywords is linear in the size of keyword fields. Boneh and Waters[65]presented a public key scheme based on hidden vector encryption that supports comparison queries, subset queries, and arbitrary conjunctive queries. The attribute values cannot be leaked after decryption. However, the ciphertext size is large because of the use of composite order bilinear groups. In addition, it has a high cost in terms of public key size and encryption operation. Fortunately, the decryption key size and decryption cost are minimized. Shi, et al. [66]proposed a scheme supporting multidimensional range query over encrypted data that can be used to share network audit logs. However, it leaks attribute values after decryption. Hwang and Lee[67]improved the size of ciphertext and private key. Kaze, et al. [68]constructed a PEKS scheme supporting disjunctive keyword search that is based on inner-product predicate encryption. However, the ciphertext size and private key size is bounded by some superpolynomial. Lai, et al. [69]introduced an efficient PEKS scheme supporting arbitrary monotone Boolean predicates that is based on key-policy attribute-based encryption (KP-ABE)[70]. ...
Multi-dimensional range query over encrypted data
1
2007
... Park, et al. [64]constructed two schemes supporting conjunctive keyword search in public key systems, in which the computation overhead is efficient and trapdoor size is constant. However, the first scheme requires a number of bilinear paring mappings and the number of private keywords is linear in the size of keyword fields. Boneh and Waters[65]presented a public key scheme based on hidden vector encryption that supports comparison queries, subset queries, and arbitrary conjunctive queries. The attribute values cannot be leaked after decryption. However, the ciphertext size is large because of the use of composite order bilinear groups. In addition, it has a high cost in terms of public key size and encryption operation. Fortunately, the decryption key size and decryption cost are minimized. Shi, et al. [66]proposed a scheme supporting multidimensional range query over encrypted data that can be used to share network audit logs. However, it leaks attribute values after decryption. Hwang and Lee[67]improved the size of ciphertext and private key. Kaze, et al. [68]constructed a PEKS scheme supporting disjunctive keyword search that is based on inner-product predicate encryption. However, the ciphertext size and private key size is bounded by some superpolynomial. Lai, et al. [69]introduced an efficient PEKS scheme supporting arbitrary monotone Boolean predicates that is based on key-policy attribute-based encryption (KP-ABE)[70]. ...
Public key encryption with conjunctive keyword search and its extension to a multi-user system
1
2007
... Park, et al. [64]constructed two schemes supporting conjunctive keyword search in public key systems, in which the computation overhead is efficient and trapdoor size is constant. However, the first scheme requires a number of bilinear paring mappings and the number of private keywords is linear in the size of keyword fields. Boneh and Waters[65]presented a public key scheme based on hidden vector encryption that supports comparison queries, subset queries, and arbitrary conjunctive queries. The attribute values cannot be leaked after decryption. However, the ciphertext size is large because of the use of composite order bilinear groups. In addition, it has a high cost in terms of public key size and encryption operation. Fortunately, the decryption key size and decryption cost are minimized. Shi, et al. [66]proposed a scheme supporting multidimensional range query over encrypted data that can be used to share network audit logs. However, it leaks attribute values after decryption. Hwang and Lee[67]improved the size of ciphertext and private key. Kaze, et al. [68]constructed a PEKS scheme supporting disjunctive keyword search that is based on inner-product predicate encryption. However, the ciphertext size and private key size is bounded by some superpolynomial. Lai, et al. [69]introduced an efficient PEKS scheme supporting arbitrary monotone Boolean predicates that is based on key-policy attribute-based encryption (KP-ABE)[70]. ...
Predicate encryption supporting disjunctions,polynomial equations,and inner products
1
2008
... Park, et al. [64]constructed two schemes supporting conjunctive keyword search in public key systems, in which the computation overhead is efficient and trapdoor size is constant. However, the first scheme requires a number of bilinear paring mappings and the number of private keywords is linear in the size of keyword fields. Boneh and Waters[65]presented a public key scheme based on hidden vector encryption that supports comparison queries, subset queries, and arbitrary conjunctive queries. The attribute values cannot be leaked after decryption. However, the ciphertext size is large because of the use of composite order bilinear groups. In addition, it has a high cost in terms of public key size and encryption operation. Fortunately, the decryption key size and decryption cost are minimized. Shi, et al. [66]proposed a scheme supporting multidimensional range query over encrypted data that can be used to share network audit logs. However, it leaks attribute values after decryption. Hwang and Lee[67]improved the size of ciphertext and private key. Kaze, et al. [68]constructed a PEKS scheme supporting disjunctive keyword search that is based on inner-product predicate encryption. However, the ciphertext size and private key size is bounded by some superpolynomial. Lai, et al. [69]introduced an efficient PEKS scheme supporting arbitrary monotone Boolean predicates that is based on key-policy attribute-based encryption (KP-ABE)[70]. ...
Expressive search on encrypted data
1
2013
... Park, et al. [64]constructed two schemes supporting conjunctive keyword search in public key systems, in which the computation overhead is efficient and trapdoor size is constant. However, the first scheme requires a number of bilinear paring mappings and the number of private keywords is linear in the size of keyword fields. Boneh and Waters[65]presented a public key scheme based on hidden vector encryption that supports comparison queries, subset queries, and arbitrary conjunctive queries. The attribute values cannot be leaked after decryption. However, the ciphertext size is large because of the use of composite order bilinear groups. In addition, it has a high cost in terms of public key size and encryption operation. Fortunately, the decryption key size and decryption cost are minimized. Shi, et al. [66]proposed a scheme supporting multidimensional range query over encrypted data that can be used to share network audit logs. However, it leaks attribute values after decryption. Hwang and Lee[67]improved the size of ciphertext and private key. Kaze, et al. [68]constructed a PEKS scheme supporting disjunctive keyword search that is based on inner-product predicate encryption. However, the ciphertext size and private key size is bounded by some superpolynomial. Lai, et al. [69]introduced an efficient PEKS scheme supporting arbitrary monotone Boolean predicates that is based on key-policy attribute-based encryption (KP-ABE)[70]. ...
Fully secure functional encryption: Attribute-based encryption and (hierarchical) inner product encryption
1
2010
... Park, et al. [64]constructed two schemes supporting conjunctive keyword search in public key systems, in which the computation overhead is efficient and trapdoor size is constant. However, the first scheme requires a number of bilinear paring mappings and the number of private keywords is linear in the size of keyword fields. Boneh and Waters[65]presented a public key scheme based on hidden vector encryption that supports comparison queries, subset queries, and arbitrary conjunctive queries. The attribute values cannot be leaked after decryption. However, the ciphertext size is large because of the use of composite order bilinear groups. In addition, it has a high cost in terms of public key size and encryption operation. Fortunately, the decryption key size and decryption cost are minimized. Shi, et al. [66]proposed a scheme supporting multidimensional range query over encrypted data that can be used to share network audit logs. However, it leaks attribute values after decryption. Hwang and Lee[67]improved the size of ciphertext and private key. Kaze, et al. [68]constructed a PEKS scheme supporting disjunctive keyword search that is based on inner-product predicate encryption. However, the ciphertext size and private key size is bounded by some superpolynomial. Lai, et al. [69]introduced an efficient PEKS scheme supporting arbitrary monotone Boolean predicates that is based on key-policy attribute-based encryption (KP-ABE)[70]. ...
Error-tolerant searchable encryption
1
2009
... 4. 3. 3 Fuzzy keyword search Bringer, et al. [71]proposed an error-tolerant searchable encryption in the context of public key that is based on functions of LSH (Locally Sensitive Hashing)[72] and BFS (Bloom Filter with Storage)[73]. An LSH function can be used to reduce the difference among similar items and a BFS function is used to answer set membership queries. If two keywords are sufficiently similar, the hash values of LSHs output is the same. Inputting the LSH values into BFS achieves error tolerant search. Their scheme has been proven PK-CKA2 secure, and protects the search pattern as well using the PIR technique. ...
Approximate nearest neighbors: towards removing the curse of dimensionality
1
1998
... 4. 3. 3 Fuzzy keyword search Bringer, et al. [71]proposed an error-tolerant searchable encryption in the context of public key that is based on functions of LSH (Locally Sensitive Hashing)[72] and BFS (Bloom Filter with Storage)[73]. An LSH function can be used to reduce the difference among similar items and a BFS function is used to answer set membership queries. If two keywords are sufficiently similar, the hash values of LSHs output is the same. Inputting the LSH values into BFS achieves error tolerant search. Their scheme has been proven PK-CKA2 secure, and protects the search pattern as well using the PIR technique. ...
Public key encryption that allows PIR queries
1
2007
... 4. 3. 3 Fuzzy keyword search Bringer, et al. [71]proposed an error-tolerant searchable encryption in the context of public key that is based on functions of LSH (Locally Sensitive Hashing)[72] and BFS (Bloom Filter with Storage)[73]. An LSH function can be used to reduce the difference among similar items and a BFS function is used to answer set membership queries. If two keywords are sufficiently similar, the hash values of LSHs output is the same. Inputting the LSH values into BFS achieves error tolerant search. Their scheme has been proven PK-CKA2 secure, and protects the search pattern as well using the PIR technique. ...
VABKS: verifiable attribute-based keyword search over outsourced encrypted data
1
2014
... 4. 3. 4 Verifiable keyword search The server is assumed semi-honest such that it may just return a part of the search results or even inaccurate results. Zheng, et al. [74]dealt with this problem with an attribute based encryption scheme called VABKS (Verifiable Attribute-Based Keyword Search). In this scheme, only the user who satisfies the data owners access control policy is allowed to perform search and verify operations. However, verifying the correctness of search results is expensive. Furthermore, the scheme is vulnerable to off-line attacks because the keyword ciphertext and the search token can be easily obtained by an adversary. Liu, et al. [75]proposed a new VABKS scheme, in which a secure channel is not necessary. Their proposed scheme is also relatively efficient in verifying the correctness and integrity of search results. ...
Efficient verifiable public key encryption with keyword search based on KP-ABE
1
2014
... 4. 3. 4 Verifiable keyword search The server is assumed semi-honest such that it may just return a part of the search results or even inaccurate results. Zheng, et al. [74]dealt with this problem with an attribute based encryption scheme called VABKS (Verifiable Attribute-Based Keyword Search). In this scheme, only the user who satisfies the data owners access control policy is allowed to perform search and verify operations. However, verifying the correctness of search results is expensive. Furthermore, the scheme is vulnerable to off-line attacks because the keyword ciphertext and the search token can be easily obtained by an adversary. Liu, et al. [75]proposed a new VABKS scheme, in which a secure channel is not necessary. Their proposed scheme is also relatively efficient in verifying the correctness and integrity of search results. ...